Airodump-ng is a network software used for capturing / sniffing the packets in the air while you are in monitor mode. It is specially suitable for collecting WEP Initialization Vectors (IVs). It shows all the wireless networks around us and show the detailed information about those networks. This tool is the basis for many hacking tools
Steps to Capture or Sniff Packets
- Enable Monitor Mode of Wireless Interface Card
-
Run airodump-ng wlan0 command in Kali Linux
where wlan0 is wireless adapter in monitor modeairodump-ng wlan0
Run airodump-ng Command in Kali Linux After running the above command it will discover all the wireless networks around me. This program will continue running unless we quit it using CTRL+C key in the Kali Linux Terminal
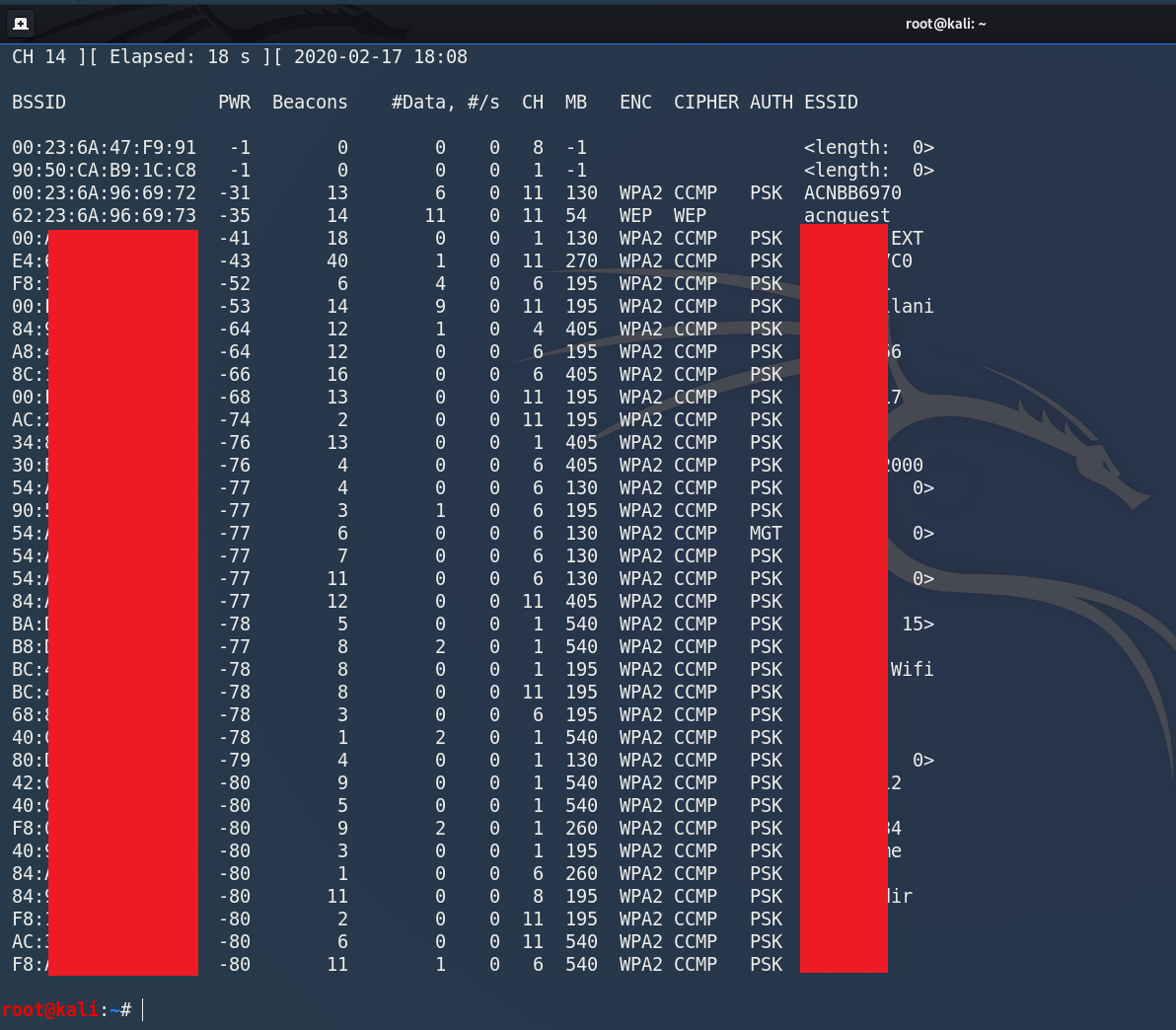
List of Wireless Networks Around me In airodump-ng wlan0 command:
- ESSID is the name of wireless networks around us
- BSSID is the MAC address of the target network
- PWR is the signal strength of the network. Higher number means we have better signal
- Beacons are frames which are sent by the network in order to broadcast its existence
- #Data is the number of data packets
- #/s is the number of data packets which are collected in the past 10 seconds
- CH is the channel on which the network is working on
- MB is the maximum speed supported by the network
- ENC is the encryption used by the network such as WEP / WPA / WPA2 / OPN
- CIPHER is the cipher used in the network
- AUTH is the authentication used on that network such as PSK (Pre-Shared Key) / MGT
-
Now i am going to target my own network named acnguest using this command:
airodump-ng --bssid 62:23:6A:96:69:73 --channel 11 --write basic_wep wlan0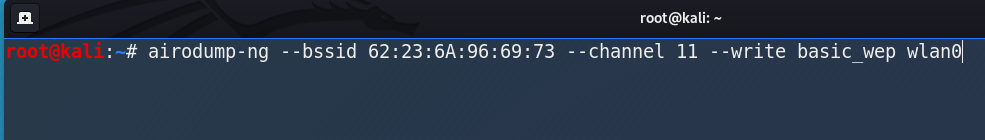
airodump-ng Command to Target the Network In airodump-ng command:
- –bssid 62:23:6A:96:69:73 is the MAC address of my target network
- –channel 11 is the channel number of my target network
- –write basic_wep is telling us to write / store all the gathered data in a file named basic_wep
- wlan0 is the name of wireless adapter in monitor mode
Now below is the detailed information of a single network (which is our targeted network). Section 1 is showing the network in which we are sniffing the data, while Section 2 show us the devices which are connected with the network in Section 1. Currently in Section 2, only 1 device is connected with the network in Section 1. MAC address of connected device is shown under the STATION (Section 2).
Now we have a new file named basic_wep-01, which contains the captured data. airodump-ng automatically append -01 with the file name. And there are multiple files created with different extensions. But the main file is basic_wep-01.cap which contains all the captured data. This file contains everything such as URLs, Usernames, Passwords, Chat Messages etc. But the main problem is that all the data is encrypted.
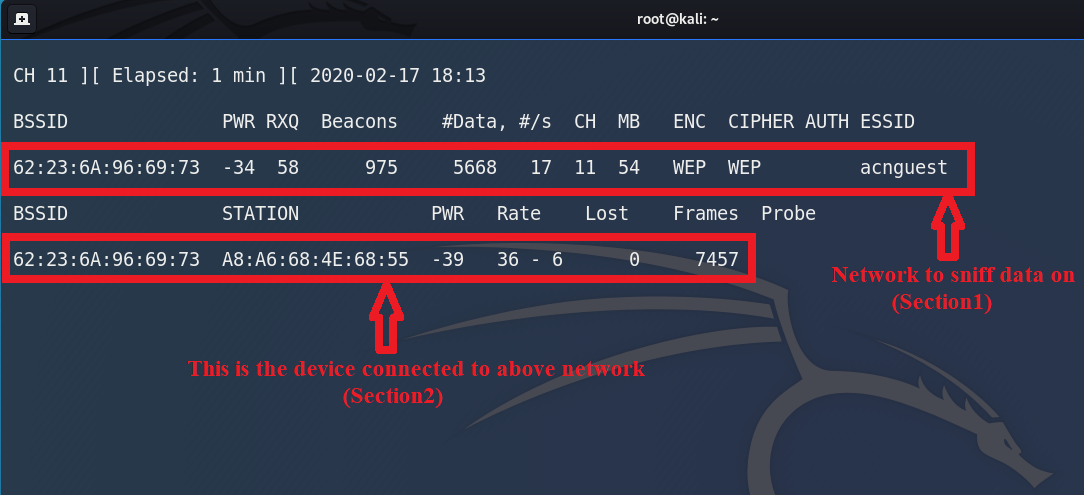
Detailed Network Information of Targeted Network using airodump-ng